Sensational Tips About How To Start Dos Attack
![What Is A Dos Attack And How To Dos Someone [Ping Of Death]](https://spanning.com/wp-content/uploads/2020/06/denial-of-service-attack-example.png)
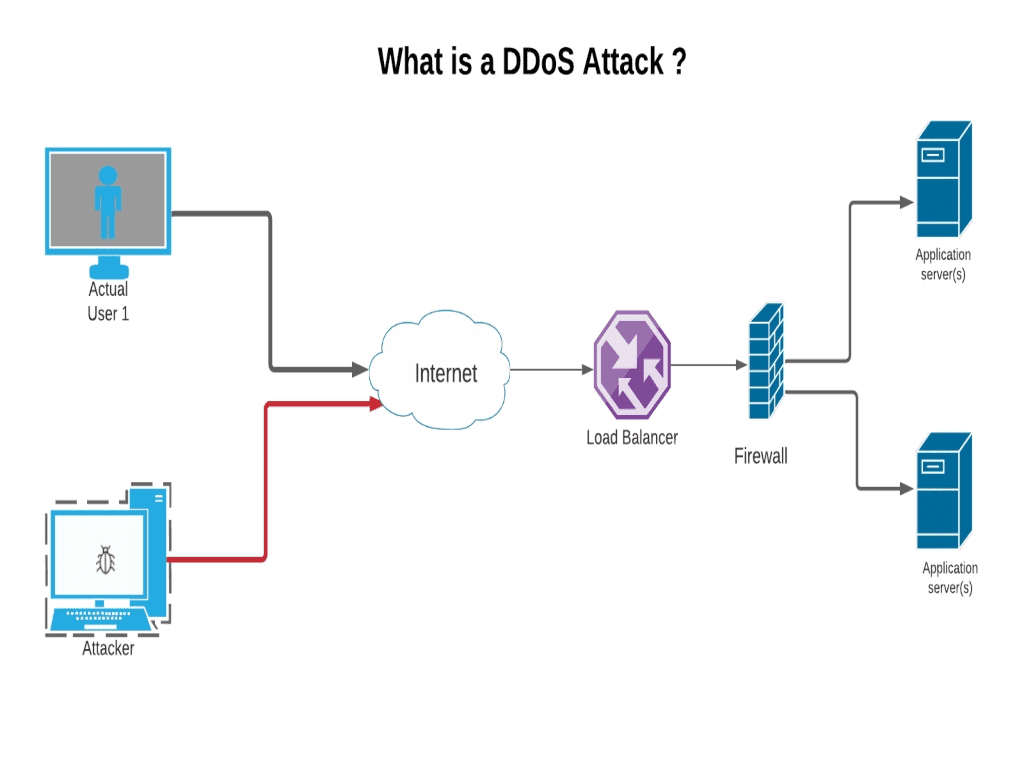
Identify gaps in security and assess potential threats to your setup.
How to start dos attack. Next, verify it is correct and. Start by selecting a target for attack by entering the url or i.p. Generally, this requires a fully managed solution which ensures that the network’s security posture is always effective and up.
It is one of the free ddos attack tools specifically used to generate. 🔵 edureka cyber security masters program: The three main types of dos attacks are:.
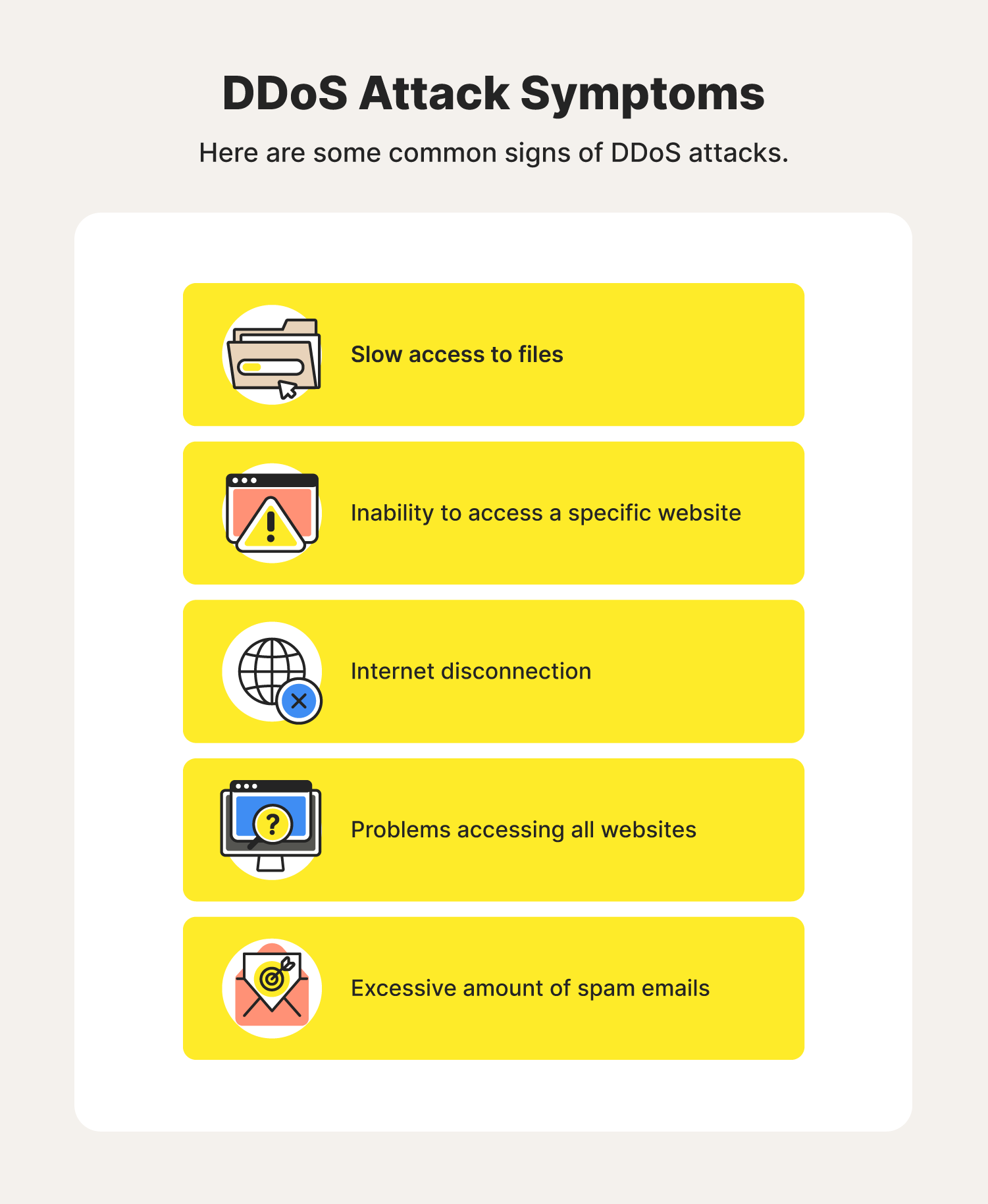
Media access control (mac) flooding is a type of ddos attack designed to overwhelm the network switch with data packets. Step 2) first we will check what is the current. 503 “service unavailable” errors should start around this time.
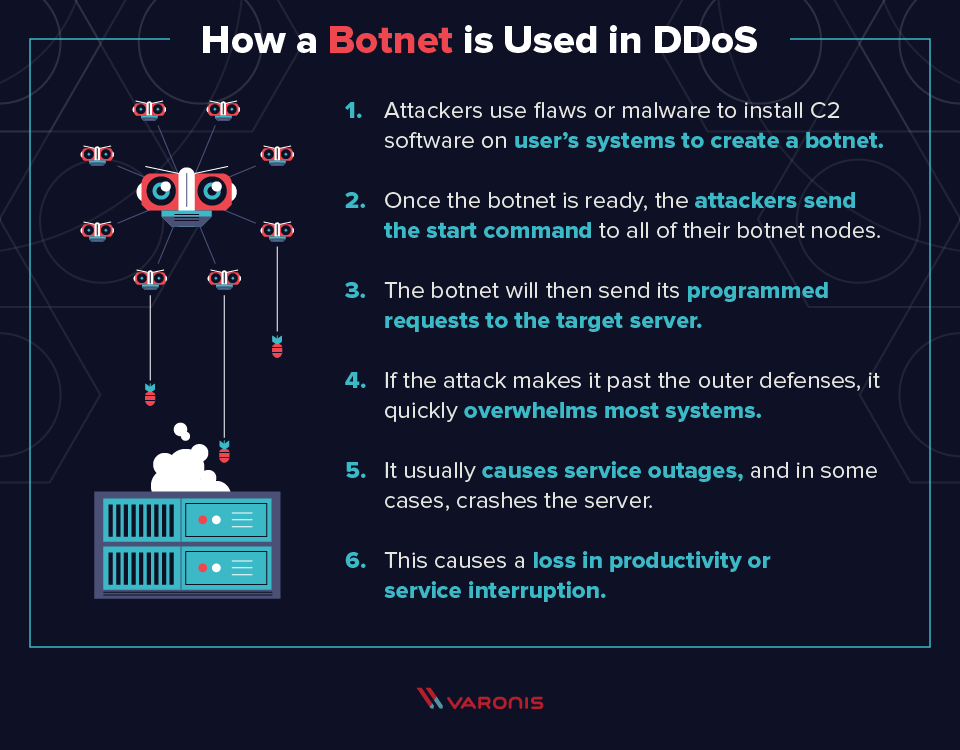
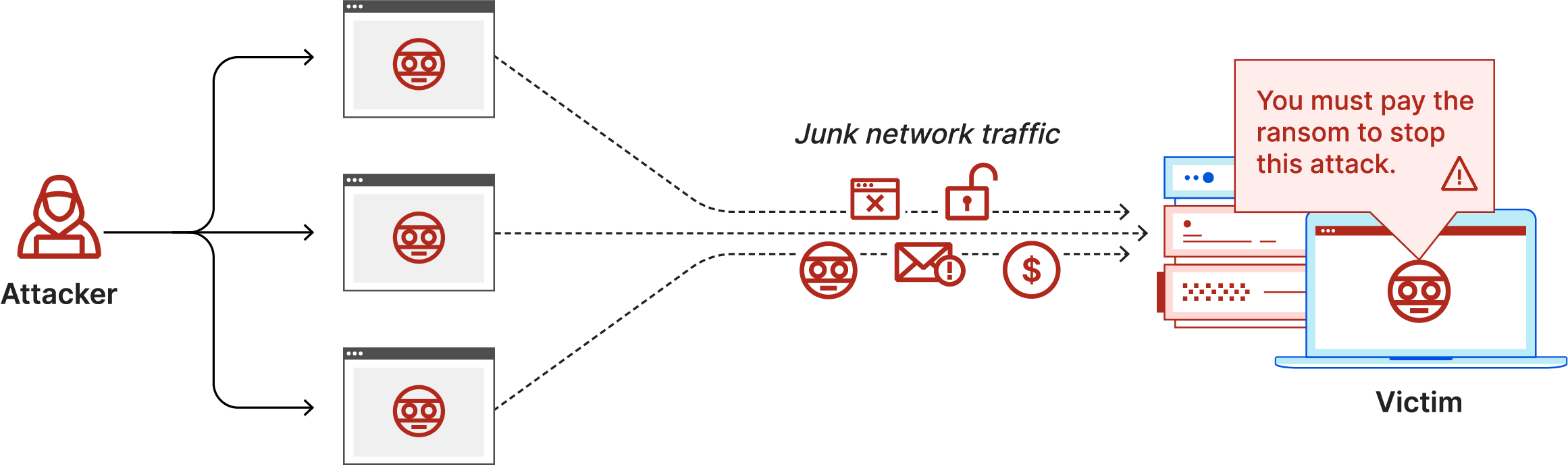
There are many ways of doing a ddos attack try them on your server or website never try them on other websites. You will notice six tabs. They can be very simple;
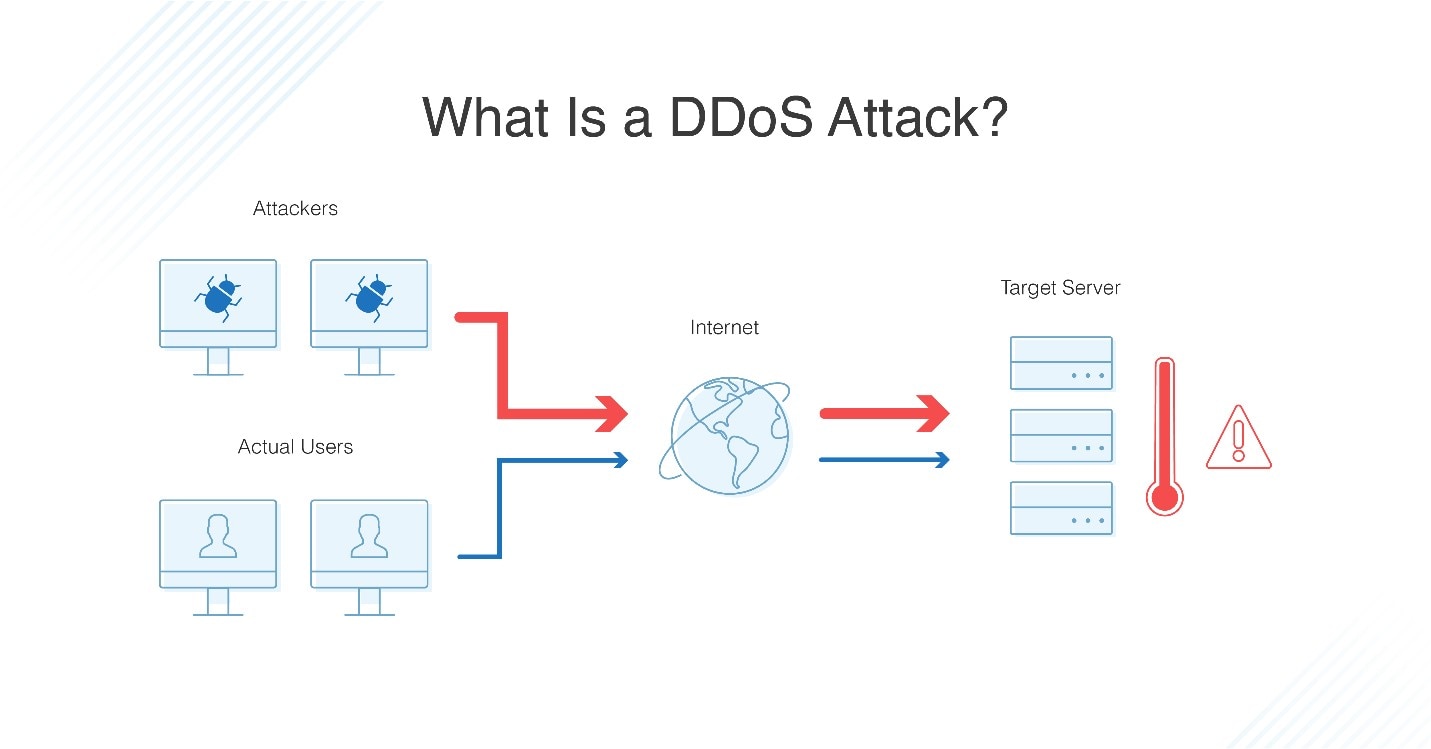
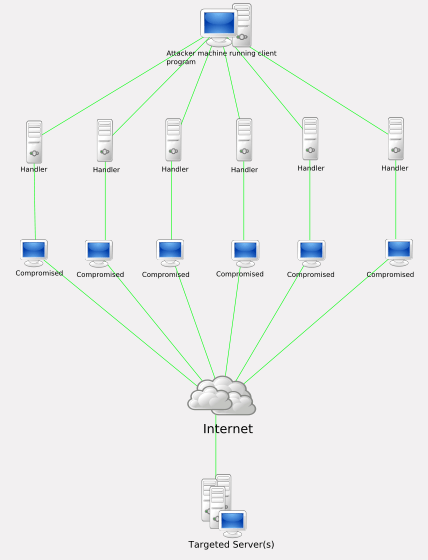
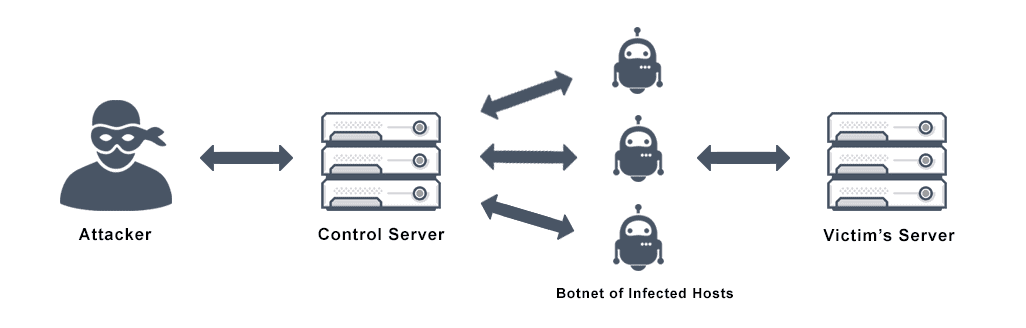
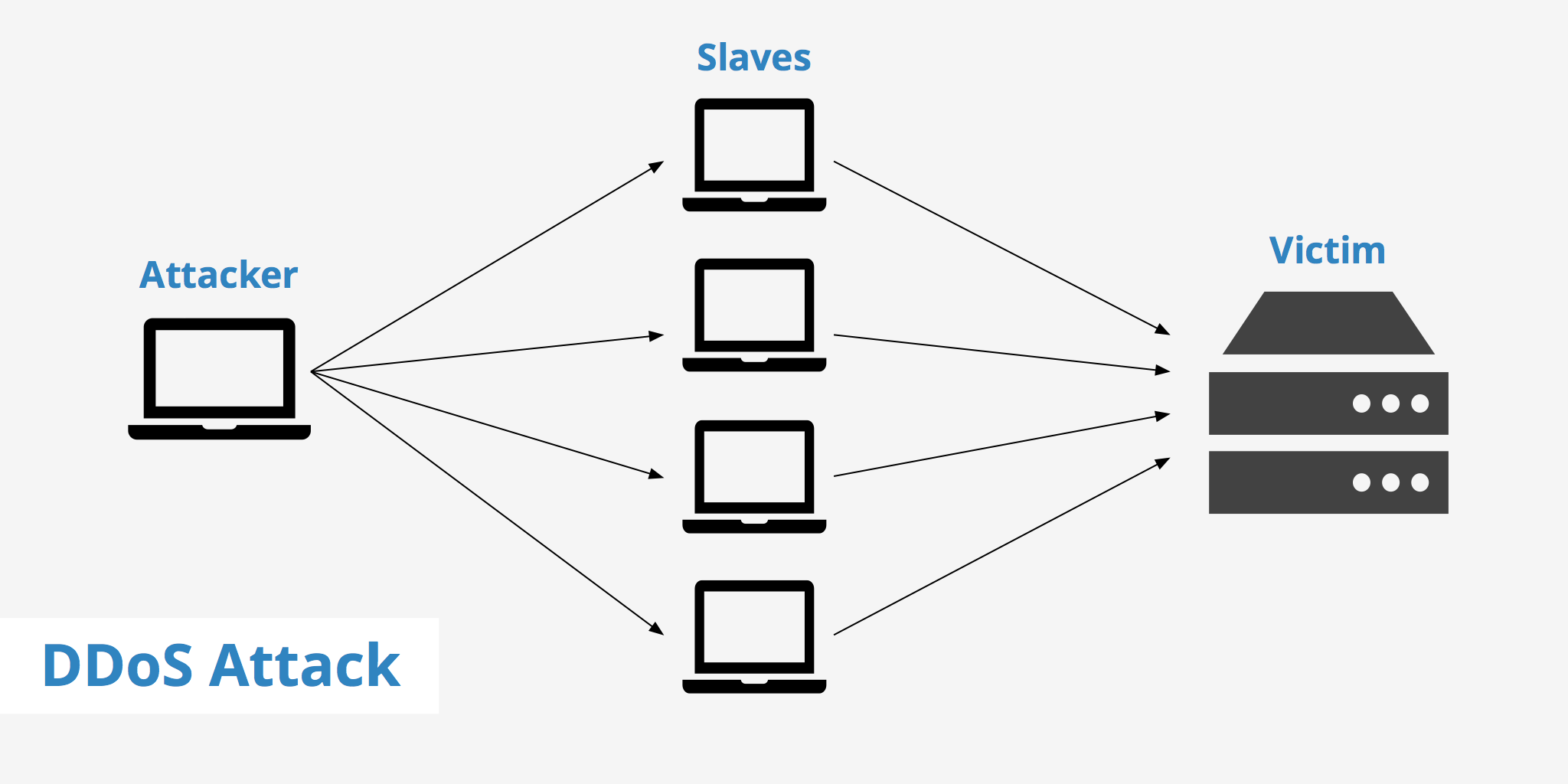
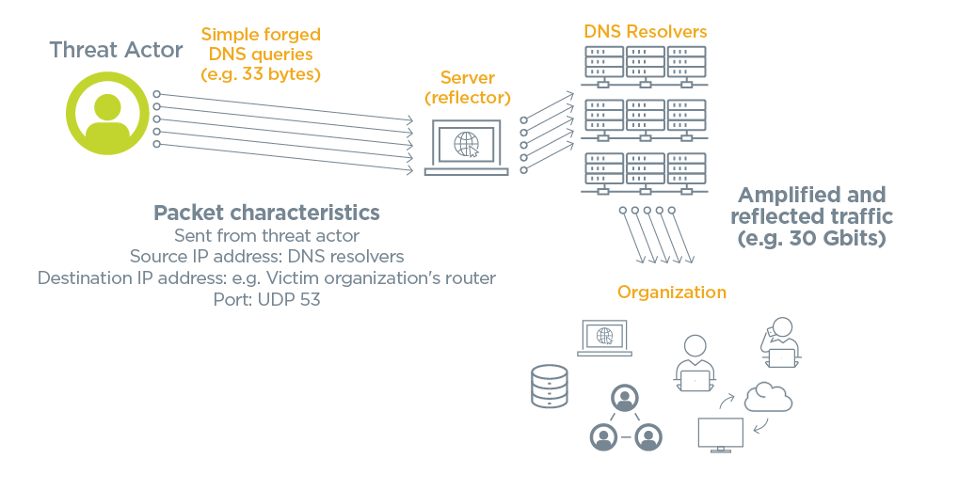
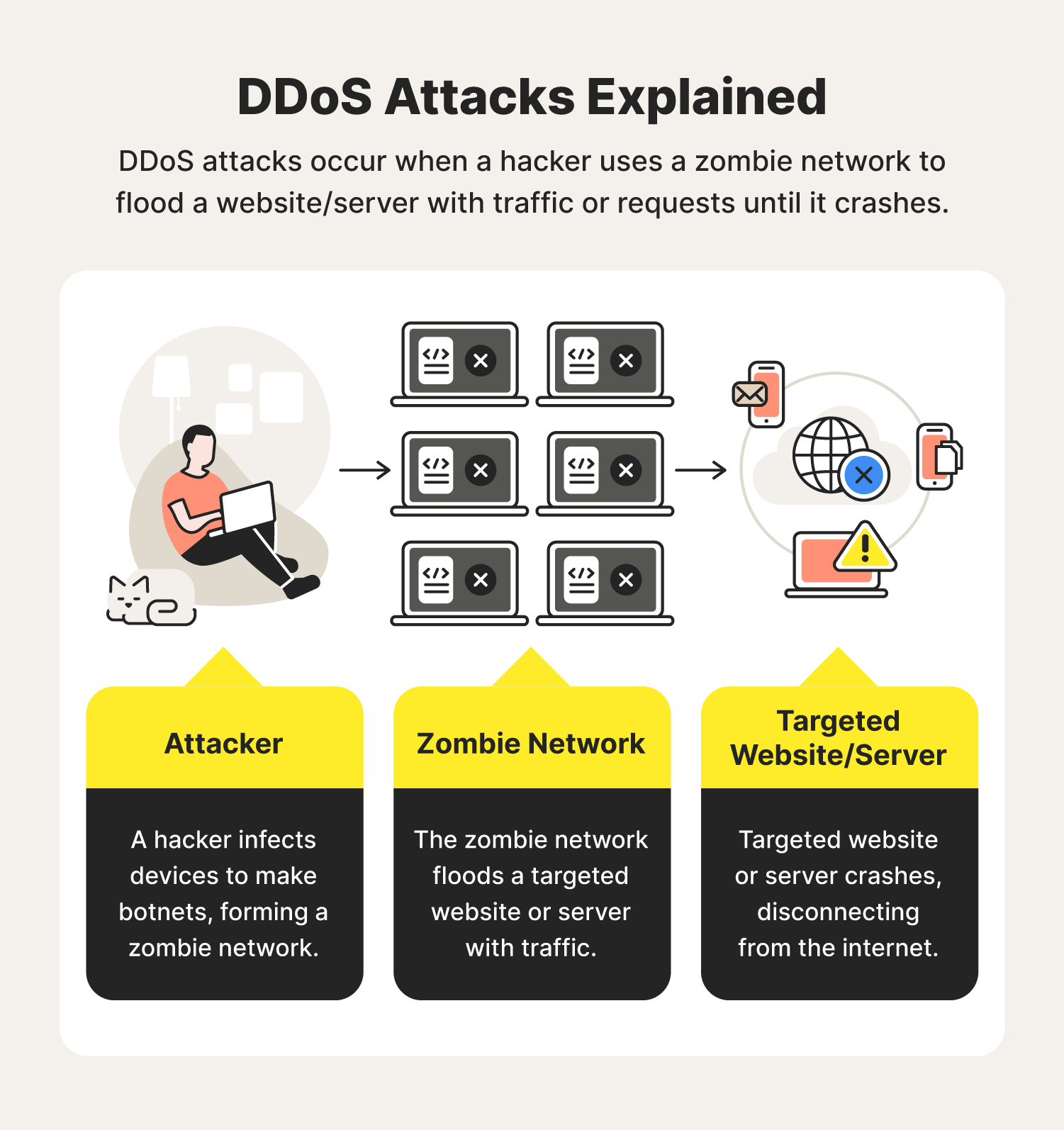
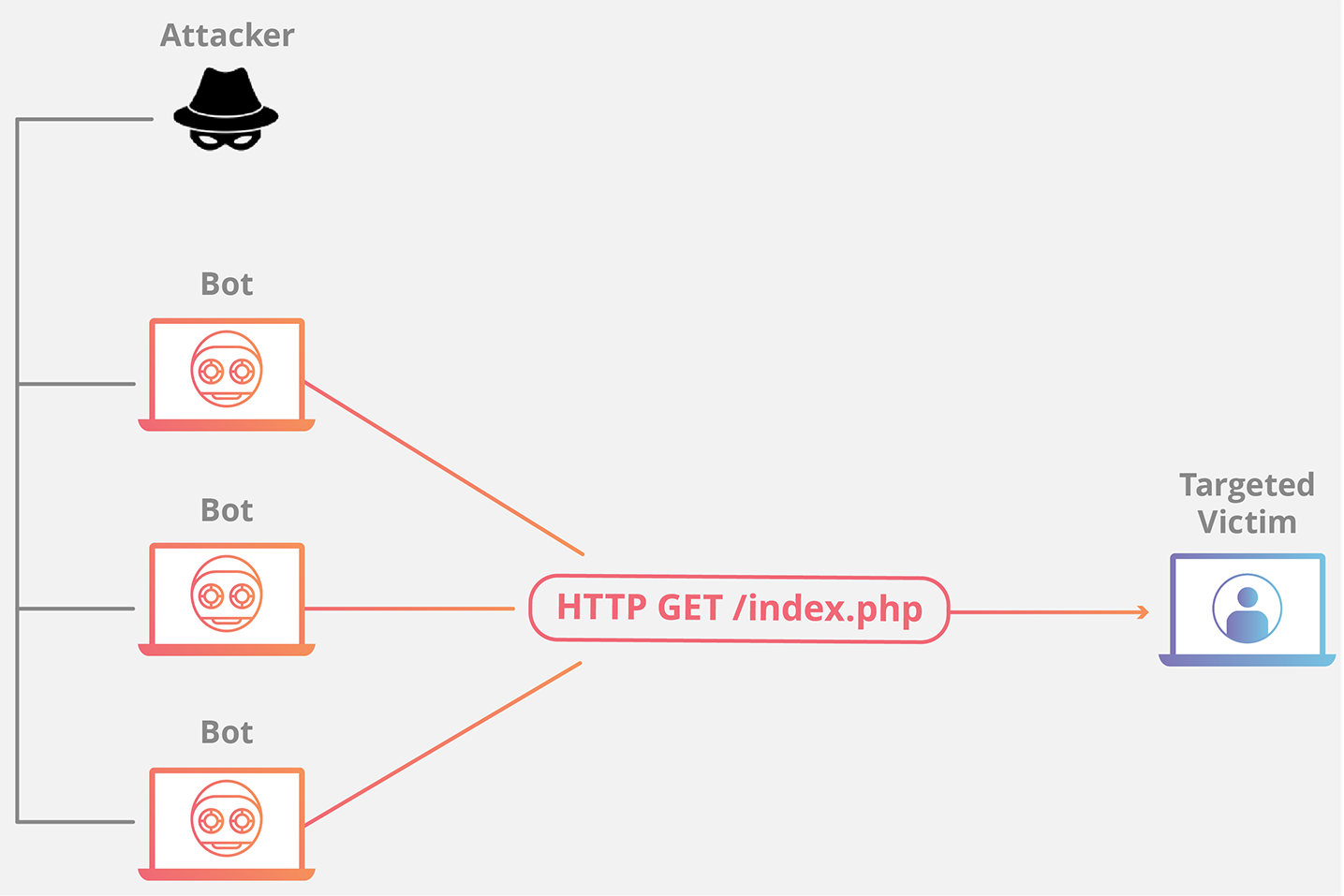
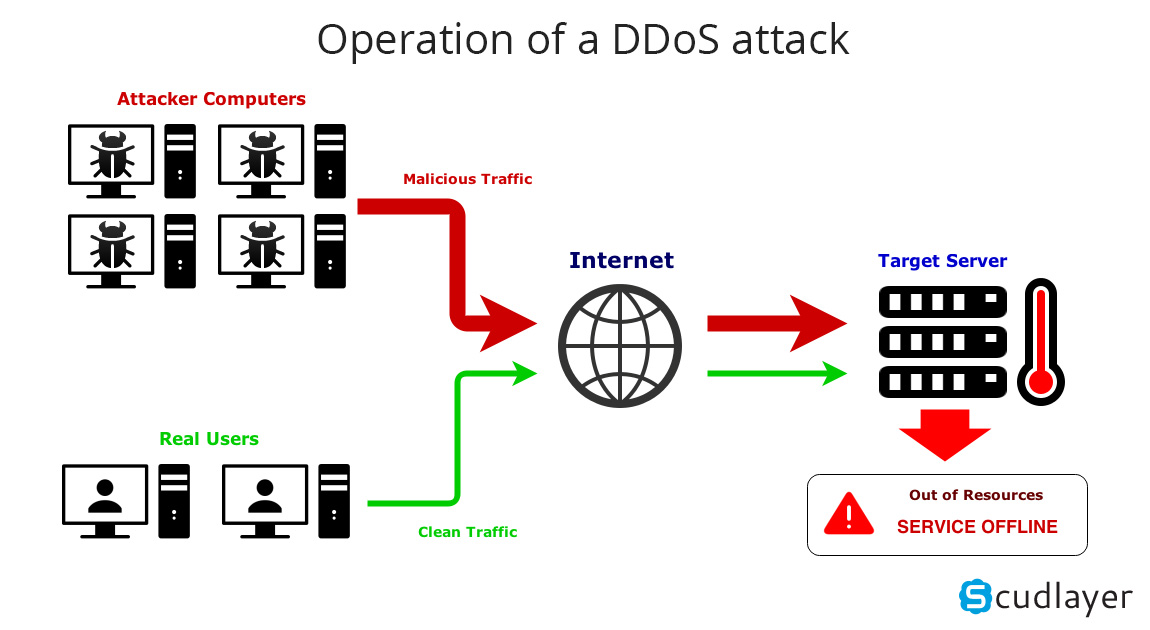
Here, to launch a distributed denial of service attack, in the ddos master system, the attacker uses botnets to affect and then control many computers and then attack a single system. Dos attacks accomplish this disruption by sending malicious traffic from a single machine — typically a computer. Dos attacks use two primary strategies to accomplish that goal.
Overwhelming a device or network with traffic. This should display the desired target. The first — and most popular — strategy is flooding:
![What Is A Dos Attack And How To Dos Someone [Ping Of Death]](https://www.guru99.com/images/EthicalHacking/DOS_Attacks.jpg)
![What Is A Dos Attack And How To Dos Someone [Ping Of Death]](https://www.guru99.com/images/EthicalHacking/DOS_Attacks1.png)
![What Is A Dos Attack And How To Dos Someone [Ping Of Death]](https://www.guru99.com/images/EthicalHacking/DOS_Attacks4.png)
![What Is A Dos Attack And How To Dos Someone [Ping Of Death]](https://www.guru99.com/images/EthicalHacking/DOS_Attacks3.png)
![What Is A Dos Attack And How To Dos Someone [Ping Of Death]](https://www.guru99.com/images/EthicalHacking/DOS_Attacks5.png)